The Five-Eyes Global Alliance sounds like something dreamt up by a spy fiction novelist. A secret international organization watching everything you do online, reading your emails and texts, collecting all this information, and sharing it without your knowledge. But this isn’t fiction – it has been happening for over 70 years.
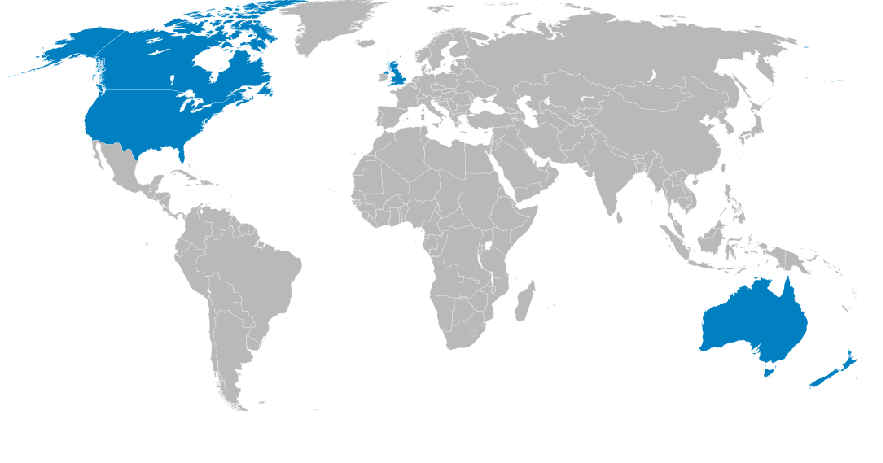
The Five-Eyes Global Alliance is the almost dystopian name for a number of clandestine information sharing agreements between the USA, UK, Australia, New Zealand, and Canada. The first started in the 1940s, to watch and decrypt Soviet Union communications, increasing government co-operation to be more effective.
As the Cold War progressed, the activities covered by these agreements expanded into all aspects of public life. Many new governments also joined. The Five Eyes grew into the Nine-Eyes and Fourteen-Eyes Alliances: a global network of the most powerful governments working together to spy on their citizens.
Until 2003, these agreements were hidden from the public, the very people being spied on. But over the last 15 years, more and more has been revealed about how exactly the Five-Eyes and their partners have been spying on us all. And what they’ve been doing with the information stolen.
In 2013, Edward Snowden leaked 1,000s of documents detailing the routine breaches of privacy and basic human rights committed by the Five-Eyes governments. For the first time since the original Alliance started, we all have the power to understand what they are up to and decide how we want to respond.
It’s vital to appreciate the fundamental aim of the Five-Eyes agreements and how this affects you. The Five-Eyes is all about accessing, monitoring, collecting and sharing private citizens’ data to better spy on them. Alliance members prefer that this happens without your knowledge. You won’t even know when they have breached your privacy or shared your information.
The motivation claimed is greater security, but it’s easy to see how this can all be used for much more sinister means. Otherwise, it would not have been a secret for so many decades. While Snowden and others have chipped away much of the secrecy around the Five-Eyes, we may never truly grasp the full extent of their activities.
Why not? 99% of internet data is shared across a vast network of fiber optic cables, stretching across the Atlantic Ocean and over entire continents. These cables were laid down and are maintained by individual governments.
For instance, most Transatlantic fiber optic cables start and end within the USA and UK. Almost all data shared across these cables is monitored and controlled by surveillance stations on coastlines at either side of the Atlantic, where the cables emerge from the ocean. In theory, this gives the UK and US governments complete access to all data passing through their fiber optic cables. Now imagine this happening in countries across the entire planet.
This is, in essence, how the Five, Nine and Fourteen-Eyes Alliances work. By using pre-existing networks that they created in the first place, governments can track and collect any data passing through those networks.
Any time you go online to buy a pair of shoes, pay your credit card bill, post a selfie, email your parents, book a flight, or decide to kill some time Googling Islamic Jihad – this can all be recorded, without you knowing. Along with your identity, physical location, even what room of the house you’re in.
When you stop to consider the implications of this, it can be terrifying. Even with the rise of social media, our online activity is still deeply personal, private, and potentially embarrassing. Most of us wouldn’t want our browsing history shared with our family, never mind the government of Denmark.
At any time, the governments of the Five-Eyes Alliances can work together and build an online profile of you; use this to spy on you in real life; or target you for extra surveillance and even arrest. All in the name of national security.
Most people don’t have to worry about suddenly having their doors knocked in by the police because of their search history. However, it would still be nice to know that you’re not being watched every second you’re online (and possibly offline, too).
As the internet has evolved and our relationship to it grown more complex, online privacy has also become more complicated. Government’s have not just been exposed for their intrusive and secret spying activities. They have also come into conflict with big tech firms, privacy groups, and their own courts over access to internet users’ private data. The recent legal battles over the encryption of smartphones and messaging apps are one example of this trend. These kinds of court cases will continue and new privacy scandals will emerge for many years to come.
Stuck in the middle of all this, is you. The innocent internet user trying to browse online without worrying about your entire life and identity being shared with – and manipulating by – complete strangers. It can feel like a lost cause, fighting to maintain some privacy online. It is the classic David vs. Goliath story. You vs. the most powerful governments in the world, with their infinite cash reserves, and a baffling array of tools at their disposal.
You can resign yourself to this reality – that you are a helpless victim in the grand scheme of government spying – or you can take a more active approach to safeguarding your privacy.
As concerns about online privacy have increased, so too have the tools and resources available to ordinary people. You can join the increasing number of private citizens fighting back and reducing the access of the Five-Eyes Alliances to their private data. This won’t just protect you from government surveillance. It will also protect you from the two other major concerns of our time: private corporations selling your data to lobbyists and advertisers; and criminal groups using it to hold you ransom or steal your identity.
Something as simple as installing a Virtual Private Network (VPN) on all your devices can immediately add many layers of privacy to your online activity. VPNs use military-grade encryption and other tools to mask your identity, location, and browsing from the wider internet, hiding you while you are online.
While VPNs are legal in most countries, it’s important to understand their relationship to the Five-Eyes governments, and what laws apply to them. Take the time to understand how privacy laws work in your country. That way, you can better protect yourself without getting into legal trouble down the line.
The year 2020 and the pandemic threw a wrench into everyone's plans. Companies that were…
AI is successful in boosting the productivity of organizations while helping them save cost and…
Suppose you battle back discomfort or other associated ailments due to sitting for lengthy periods…
In November 2023, investor Maksym Krippa acquired the Parus Business Center, redefining the commercial real…
Programmers create computer programs, mobile solutions and also analyse the needs of their clients and…
A trip to Santiago is sure to be memorable by default as simply seeing this…